Hi Readers, My name is Sunain and this is Windows Privilege Escalation from my viewpoint. I will discuss many ways to escalate privileges on Windows-based machines during this series.
In the last article of this series, we were done with gathering some crucial data about our Target. From now on we will use that data to make our way to NT Authority/system.
There are many attack vectors present inside a target machine we will learn about how to compromise some of them.
Note that some of the attack Vectors are more common to spot in a real-life Pentest while some are just for CTF
For Your convenience, I've made a Mindmap that would Make a sort of checklist, do check it out!
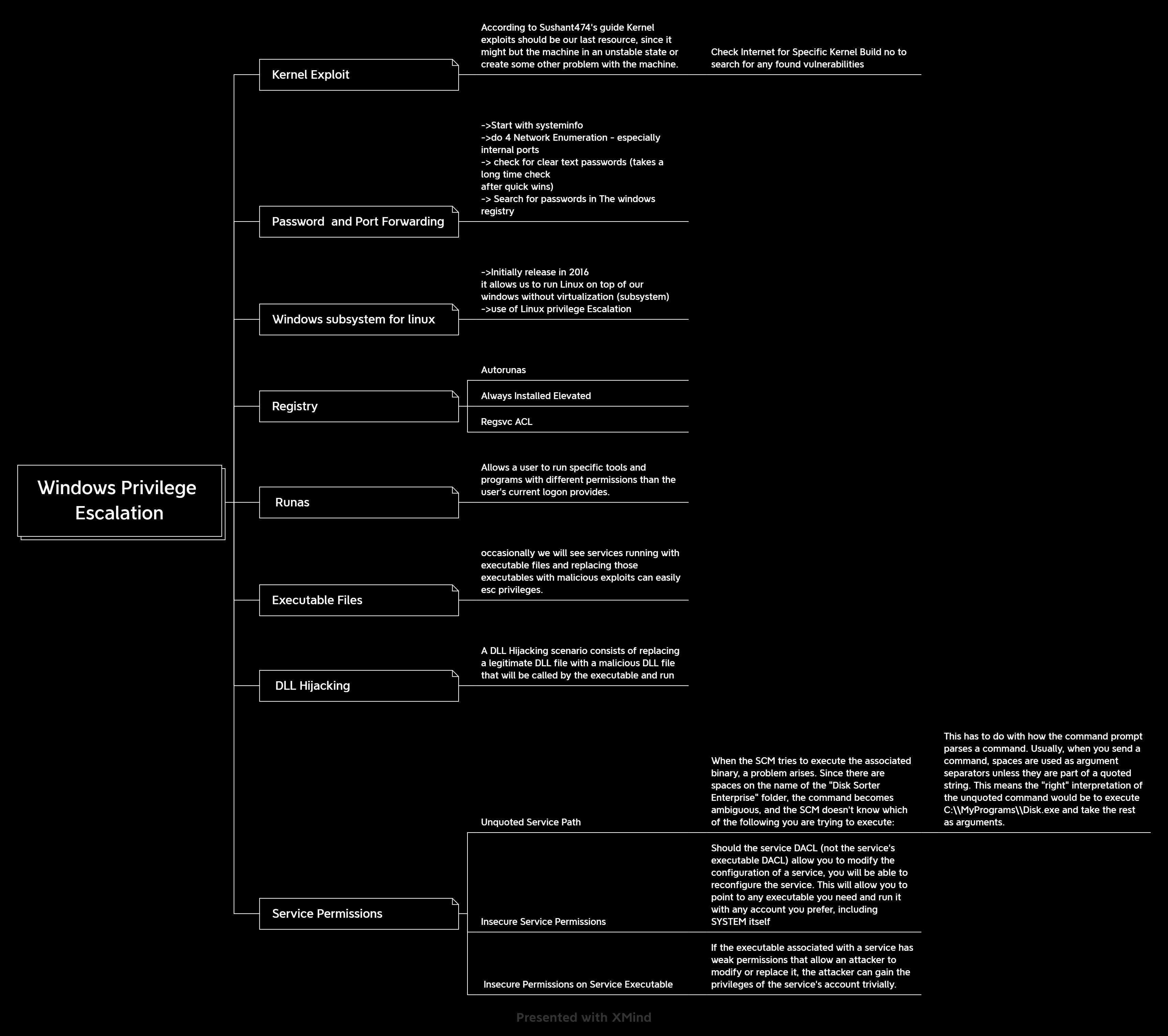
Escalation Paths
Kernel Exploit
According to Sushant474's guide Kernel exploits should be our last resource since they might put the machine in an unstable state or create some other problem with the machine.
->Check the Internet for Specific Kernel Build no to search for any found vulnerabilities
Password and Port Forwarding
Start with systeminfo ->do Network Enumeration - especially internal ports -> check for clear text passwords (it takes a long time to check after quick wins) -> Search for passwords in the windows registry
Windows Subsystem for Linux
->Initially released in 2016 it allows us to run Linux on top of our windows without virtualization (subsystem) ->use of Linux privilege Escalation
Registry
1 Autorunas
2 Always Installed Elevated
3 Regsvc ACL
Runas
Allows a user to run specific tools and programs with different permissions than the user's current logon provides.
Executable Files
occasionally we will see services running with executable files and replacing those executables with malicious exploits can easily escalate privileges.
DLL Hijacking
A DLL Hijacking scenario consists of replacing a legitimate DLL file with a malicious DLL file that will be called by the executable and run
Service Permissions
1 Unquoted Service path
When the SCM tries to execute the associated binary, a problem arises. Since there are spaces on the name of the "Disk Sorter Enterprise" folder, the command becomes ambiguous, and the SCM doesn't know which of the following you are trying to execute:
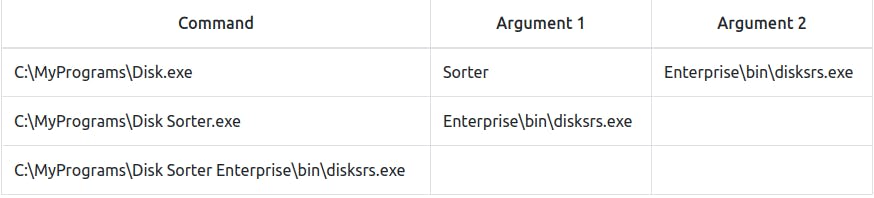
This has to do with how the command prompt parses a command. Usually, when you send a command, spaces are used as argument separators unless they are part of a quoted string. This means the "right" interpretation of the unquoted command would be to execute C:\MyPrograms\Disk.exe and take the rest as arguments.
2 Insecure Service Permissions
Should the service DACL (not the service's executable DACL) allow you to modify the configuration of a service, you will be able to reconfigure the service. This will allow you to point to any executable you need and run it with any account you prefer, including SYSTEM itself
3 Insecure Permissions on Service Executable
If the executable associated with a service has weak permissions that allow an attacker to modify or replace it, the attacker can gain the privileges of the service's account trivially.
That's it for today we are done with Windows Privilege Escalation! Thank you for reading. Sorry for Being so late. Signing off.
References sushant747 Blog Windows privesc arena
