Privilege Escalation - Enumeration (Part 2)
Series -> A Beginner's Guide on Windows Privilege Escalation.
Hi Readers My name is Sunain and this is Windows Privilege Escalation from my viewpoint. During this series, I will discuss many ways to escalate privileges on Windows-based machines.
In the last article of this series, we gathered some crucial data about Systems as well as users. Some of that data contains OS version, patches/hotfixes installed on the machine, the total number of users, username, user privileges, etc.
During this article, we will continue our Journey of enumeration by gathering some information about networks as well as Antivirus with some Password Hunting, and at last, I will tell about some Automated cool tools which can do the same.
Always remember no Automated tool can achieve things you can do Manually.
Network Enumeration
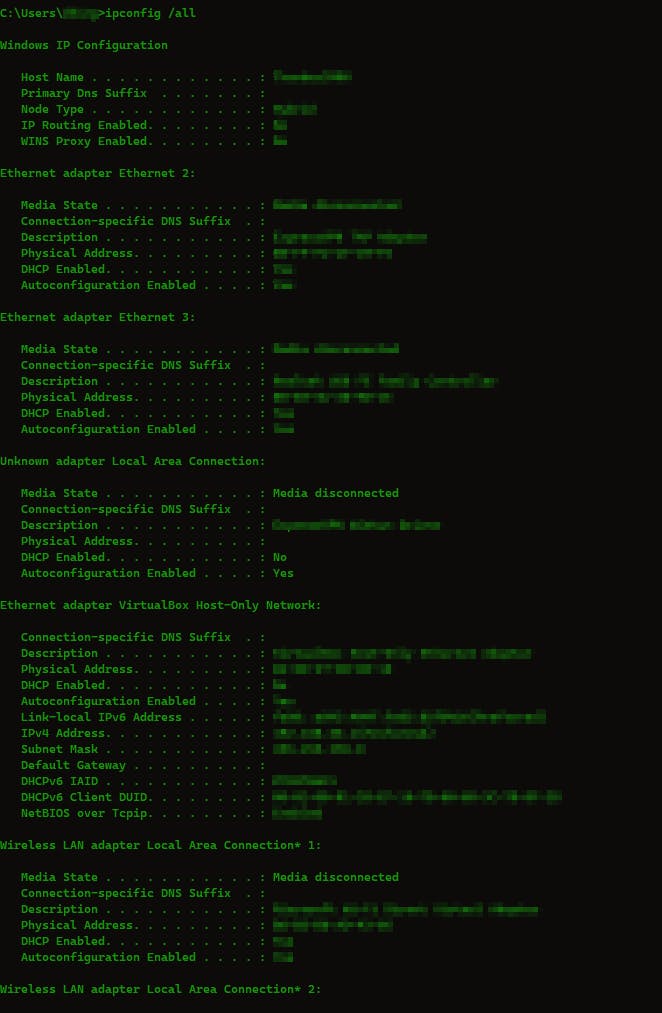
ipconfig /all: Ipconfig is the windows command for ifconfig. It will spit out all the information about the network.
arp -a: Arp table
an ARP table is simply the method for storing the information discovered through ARP. It’s used to record the discovered MAC and IP address pairs of devices connected to a network. Each device that’s connected to a network has its own ARP table, responsible for storing the address pairs that a specific device has communicated with.
It can be useful for pivoting purposes
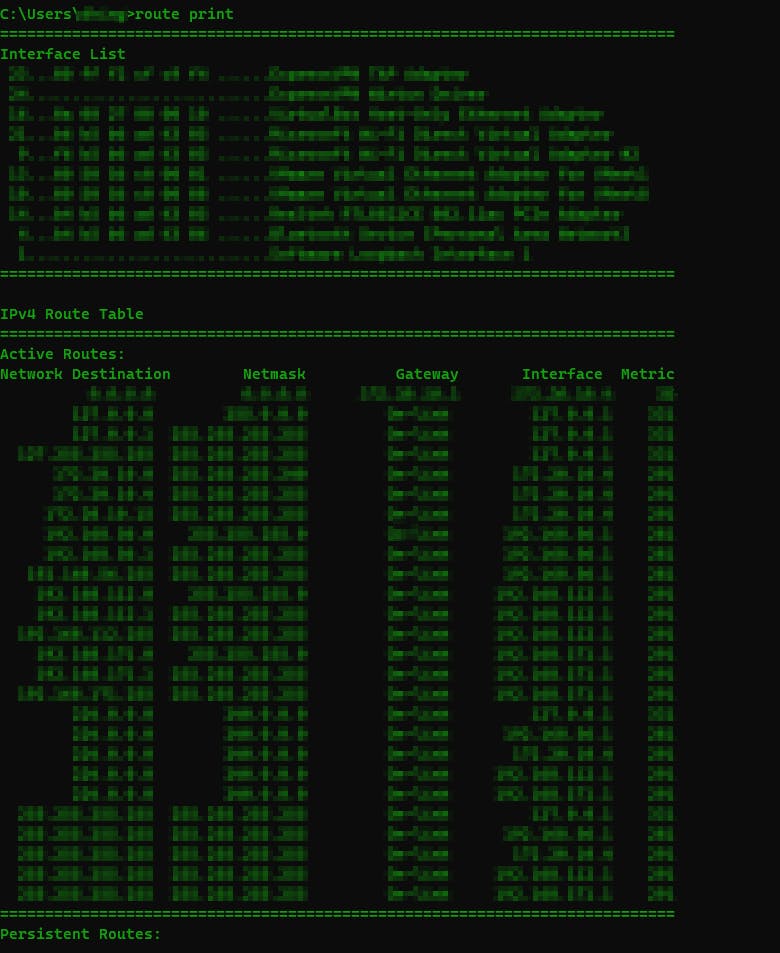
route print: Prints routing table
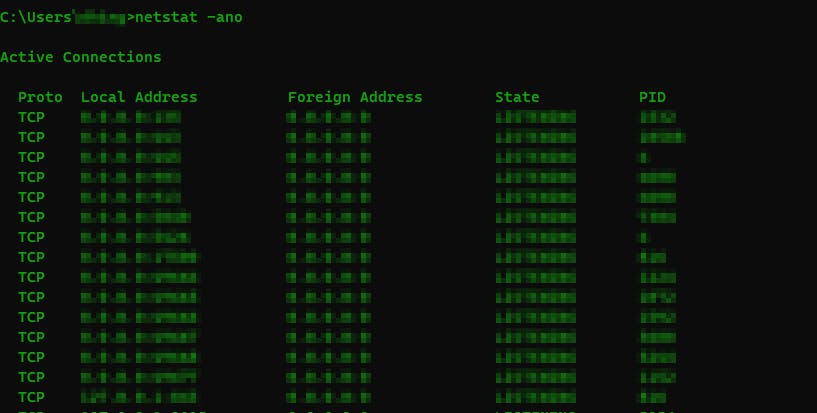
netstat -ano: Services running
Maybe you can find any service running internally.
ipconfig /all
arp -a
route print
netstat -ano
Anti-Virus Enumeration
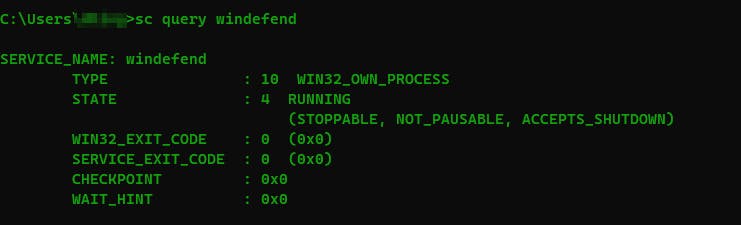
sc query windefend: Checking the status of Windows Defender
sc queryex type=service: Status of service running on the machine
Password Hunting
Search for them
findstr /si password *.txt
findstr /si password *.xml
findstr /si password *.ini
Find all those strings in config files.
dir /s *pass* == *cred* == *vnc* == *.config*
Find all passwords in all files.
findstr /spin "password" *.*
findstr /spin "password" *.*
In Files
These are common files to find them in. They might be base64-encoded. So look out for that.
c:\sysprep.inf
c:\sysprep\sysprep.xml
c:\unattend.xml
%WINDIR%\Panther\Unattend\Unattended.xml
%WINDIR%\Panther\Unattended.xml
dir c:\*vnc.ini /s /b
dir c:\*ultravnc.ini /s /b
dir c:\ /s /b | findstr /si *vnc.ini
In Registry
//VNC
reg query "HKCU\Software\ORL\WinVNC3\Password"
//Windows autologin
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
//SNMP Parameters
reg query "HKLM\SYSTEM\Current\ControlSet\Services\SNMP"
//Putty
reg query "HKCU\Software\SimonTatham\PuTTY\Sessions"
//Search for the password in the registry
reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
Enough with manual findings now time to look for some Automated scripts that can help you with the same.
Winpeas
Most of the time as soon as getting a shell you will run winpeas. Winpeas Is a great tool. I personally like the feature that it highlights the important stuff.
some other tools that might help
That's it for today we are done with Enumeration now we will move on to different Escalation paths.
until then happy hacking!
Thank you for reading.
Signing off.
