Privilege Escalation - Enumeration (Part 1)
Series -> A Beginner's Guide on Windows Privilege Escalation.
Hi Readers My name is Sunain and this is Windows Privilege Escalation from my viewpoint. During this series, I will talk about many ways to escalate privileges on Windows-based machines.
You cannot defeat your enemy until you know who they are. ~ Anthony Horowitz
To escalate your privileges around the target you must know some fundamental information about the system environment, User, Network
There can be a lot of information available and it can be overwhelming at first glance
let me help you with what you can look for and how it can be helpful.
System enumeration
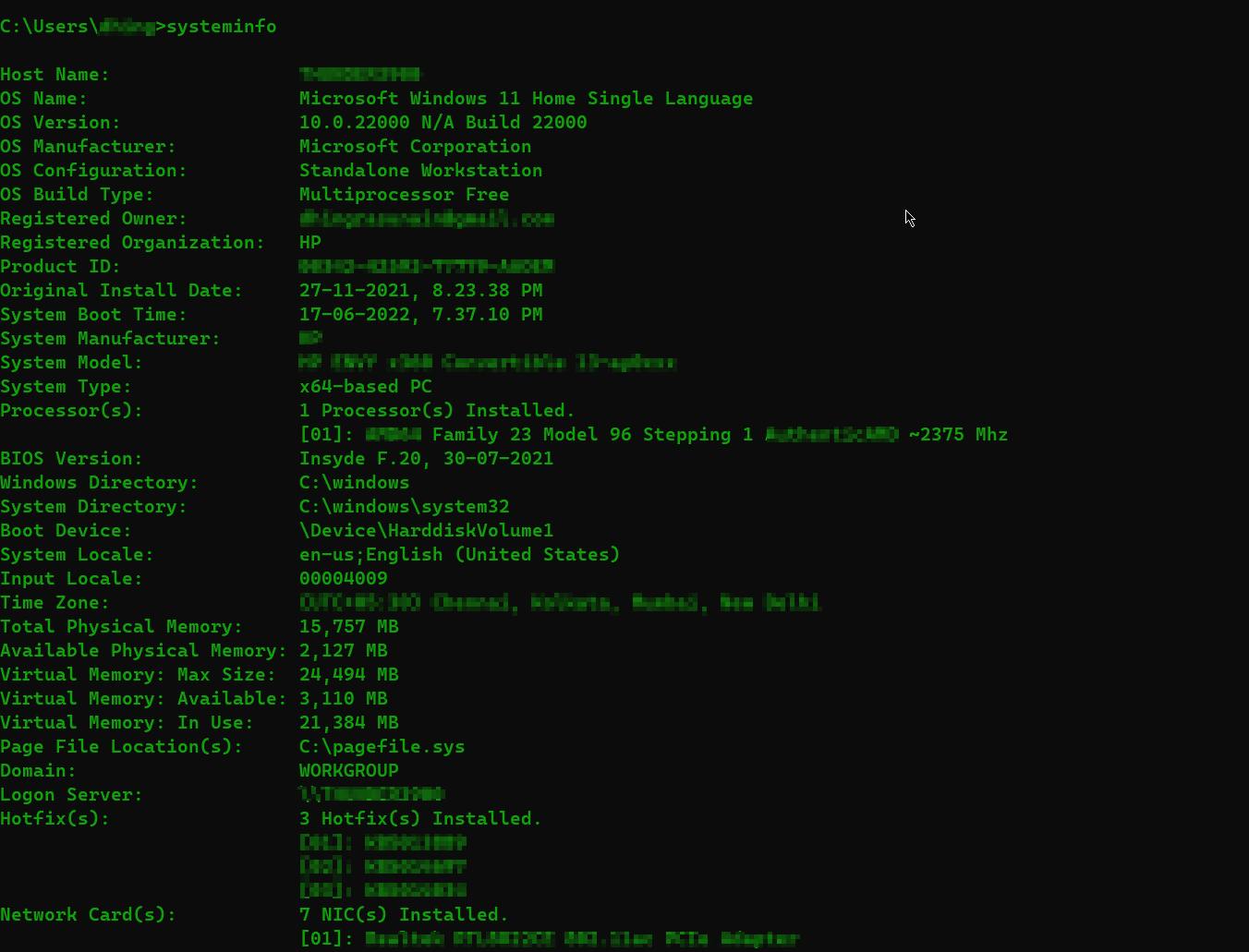
Systeminfo: this command will bombard some basic yet necessary details of the environment
Craft this command to extract some juicy information.
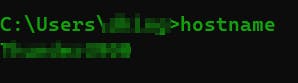
Hostname: simply displays the hostname portion of the full computer name of the computer.
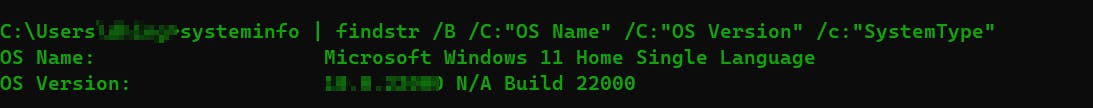
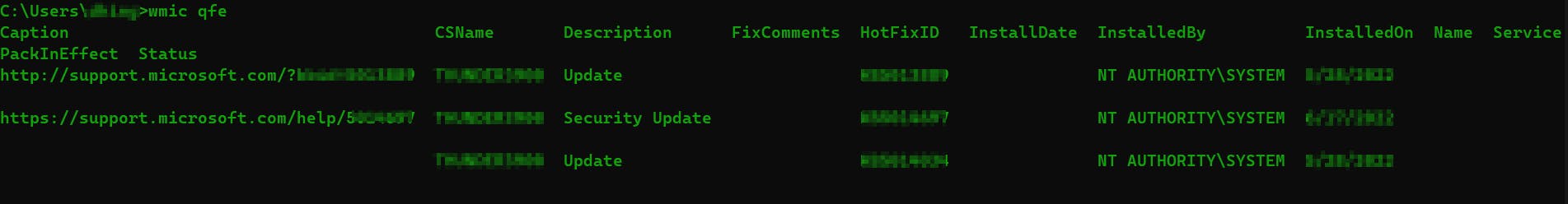
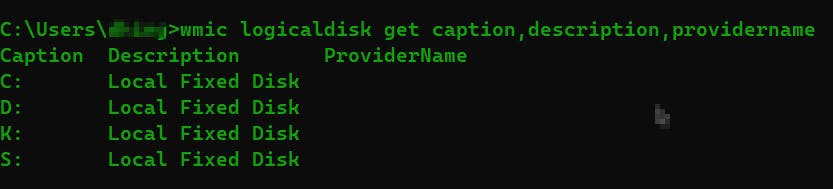
wmic qfe: this command displays system patching information which can be helpful to know what kind of patches are installed and what was the last patch. / logicaldisk will show you information about disk drives
systeminfo
systeminfo | findstr /B /C:”OS Name” /C:”OS Version” /c:”SystemType”
hostname
wmic qfe
wmic logicaldisk get caption,description,providername
User enumeration
whoami: It displays the username. this command has some interesting arguments providing some juicy information
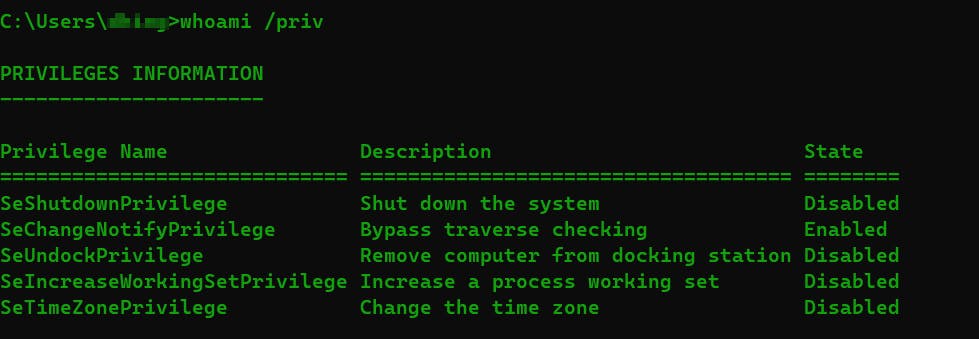
whoami /priv: tells about user privileges
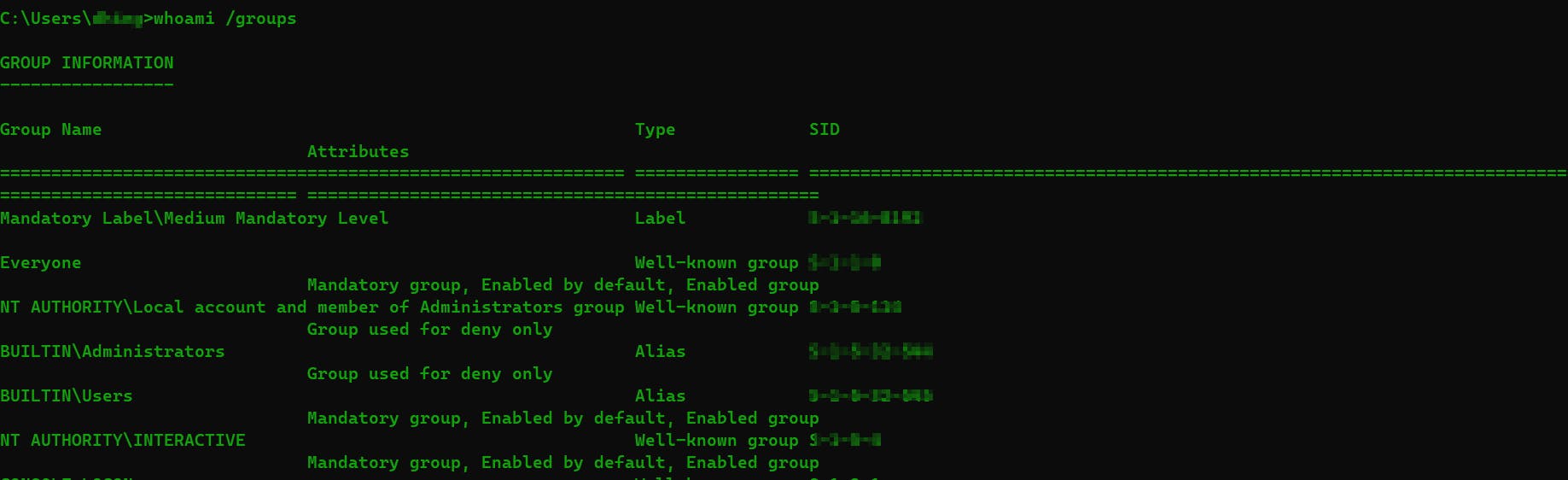
whoami /groups: Groups that the user belongs to
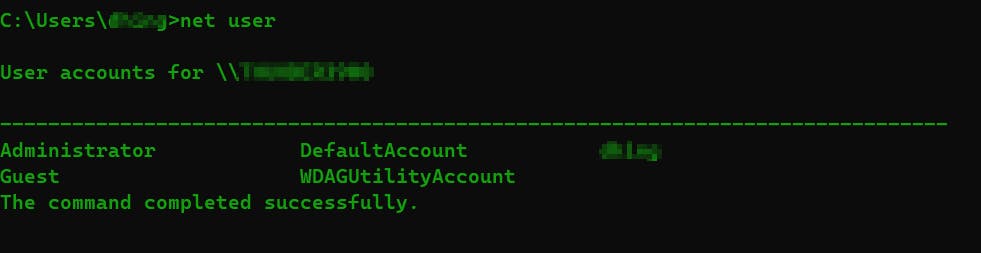
net user: All the users of the machine
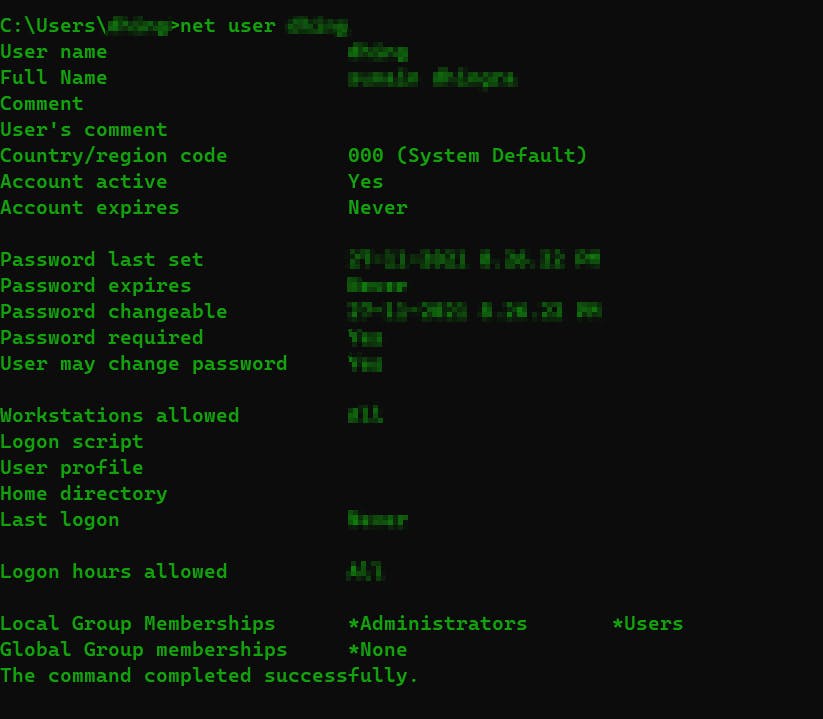
net user : view information regarding particular user
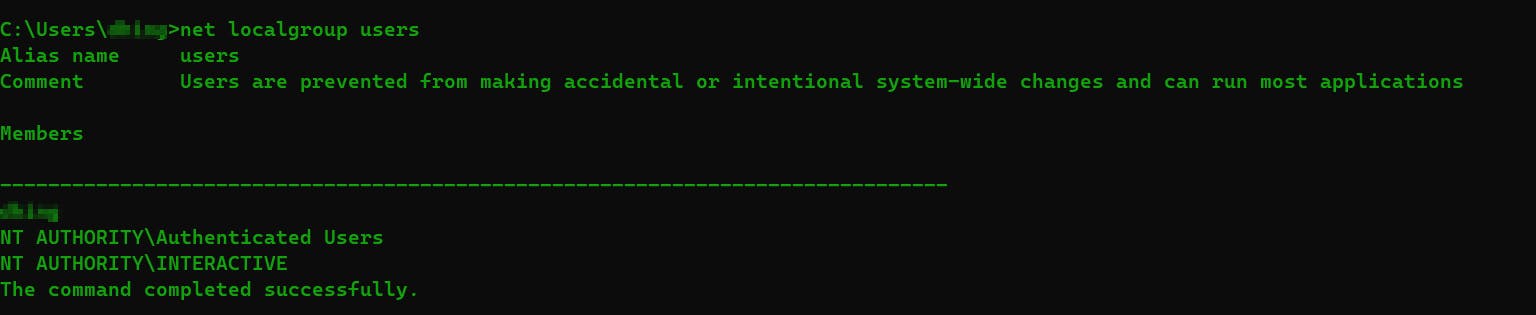
net localgroup : view members list of any particular group
whoami
whoami /priv
whoami /groups
net user
net user <username>
net localgroup <Group name>
That's it for today we will continue Enumeration in the second part of this article
until then happy hacking!
Thank you for reading.
Signing off.
